虽然oracle公司自有一套丰富的数据库产品线, 包括 oracle advanced security, VDP , Database vault , lable security , Database FireWall 等等。
但我们还是有必要关注一些第三方的 安全工具, 这些安全工具的主要用途 包括: 漏洞扫描,风险评估,安全建议,审计等。
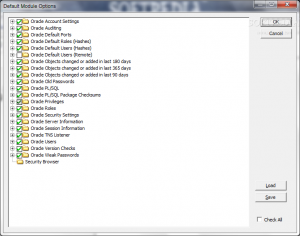
Secure Oracle Auditor - Secure Bytes 的产品 图形化的集中式审计工具, 可以自定义审计策略; 并分析数据库风险,
产品主页: http://www.secure-bytes.com/soa.php
软件截图:
Oracle Database Encryption Wizard For Oracle – Relational Database Consultants, Inc (RDC)的产品 主要功能是 数据加密, 支持 AES256 and DES3 Encryption加密算法 , 在从版本7开始支持Oracle 11gR2 及HSM( Hardware Security Modules )。
产品主页:http://www.relationalwizards.com/html/ora_encyrption.html
软件截图:
DB Protect – AppSecInc 的产品 , 提供企业级 的数据安全方案, 功能包括 隔离敏感数据库, 发现及修正可能存在的数据风险, 控制企业员工的数据访问权限, 监控越权行为等。
产品主页: http://www.appsecinc.com/products/dbprotect/index.shtml
软件截图:
NGS SQuirreL for Oracle – NGS secure 的产品 , 算是已经在国内比较知名的 oracle 风险评估漏洞扫描工具, 支持从oracle 7.3 到 11g的主要版本。
产品主页: http://www.ngssecure.com/services/information-security-software/ngs-squirrel-for-oracle.aspx
产品介绍:
Oracle数据库安全漏洞扫描工具——NGSSQuirreL for Oracle
NGSSQuirrel for Oracle是国际顶级的数据库安全漏洞扫描工具。深圳市九州安域科技有限公司是NGSSQuirrel for Oracle数据库安全漏洞扫描工具中国区授权代理。
NGSSQuirreL for Oracle支持Oracle 8i,9i和10g,并且可以检查几千个可能存在的安全威胁、补丁状况、对象和权限信息、登陆和密码机制、存储过程以及启动过程。NGSSQuirrel提供强大的密码审计功能,包括字典和暴力破解模式。
NGSSQuirrel
1. 专业数据库漏洞评估工具;
支持MSSQL Server,Oracle,Informix,DB2,MySQL ,Sybase ASE数据库
支持对数据库所有实例的特权、角色、表单、视图、存储过程等进行安全检测。
2. 用于保护基础数据库平台安全并确保数据库满足安全法规的要求;
3. 创建Lockdown脚本,用于自动修复数据库扫描中未发现的漏洞
4. 通过check selection功能,可实行具体扫描或针对目标客户的扫描。
可以为特定目标扫描存储某一定制模板
可根据具体合规性扫描选择合规性模板
5. 提供业界专业的数据库安全资讯以及安全教材。
NGS SQuirreL 数据库扫描检测内容:
1. 扫描数据库默认口令、弱口令
2. 检测触发器、存储程序、表单、包等的访问权限
3. 识别默认Object的漏洞
4. 利用密码哈希值运行密码审计
5. 审查密码策略
6. 审查数据库的版本以及补丁情况
7. 检查数据库所有安全配置以及安全审计配置
8. 针对所有发现的安全问题提供修复建议
9. 可针对单一数据库或单一实例进行扫描
NGS SQuirreL for Oracle, SQL Server, MySQL, DB2 & Informix 行业合规性审计
NGS扫描器其内置有如下所有的合规性模块:
PCI DSS(支付款行业数据安全标准V1.2或V2.2)
SOX
HIPAA
Gramm-Leach Bliley Act
FISMA
SANS Top 20
CIS Benchmark for Oracle 9i/10g Ver. 2.0
CIS Benchmark for SQL Server 2005 v1.0
CIS Benchmark for MySQL v1.0.2
Oracle 基准
NSA SQL Server 2000 V1.5 安全配置和管理指南
这些模板都会保持持续更新;NGS 审计客户将满足这些标准的要求
NGSSQuirrel for Oracle 目前在国内有 九州安域 和 XLSoft 2家代理。
软件截图:
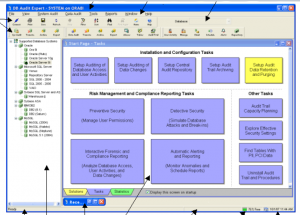
DB Audit – SoftTree的产品 功能强大的数据库安全和审计产品, 支持Oracle, Sybase, DB2, MySQL, Microsoft SQL Server等主流数据库。 DB Audit Expert是一款专业的数据库安全评估,审计和提供解决方案的数据库管理系统。DB Audit Expert允许数据库及系统管理员,安全管理员,审计人员和操作人患跟踪和分析数据库的活动,包括对数据库的访问,使用,对象的建立,修改和删除等。 DB Audit真正独特的是它内置多个审计方式,让您灵活地选择最适合你的数据库安全性要求的审计方式。
产品主页:http://www.softtreetech.com/
产品介绍
DB Audit Expert是一款专业的数据库安全评估,审计和提供解决方案的数据库管理系统。DB Audit Expert允许数据库及系统管理员,安全管理员,审计人员和操作人患跟踪和分析数据库的活动,包括对数据库的访问,使用,对象的建立,修改和删除等。DB Audit真正独特的是它内置多个审计方式,让您灵活地选择最适合你的数据库安全性要求的审计方式。
主要优势:
提高系统的安全性并确保系统问责制。
捕获常规和“后门”访问被审计的数据库系统。
从易于管理的单一位置,集中了安全和审计控制多个数据库系统的功能,
统一审计的图形界面功能,缩短了学习曲线,很容易使用。
提供分析报告,全面总结概括,减少审核大量数据从而使轻松地识别各种数据库的安全性侵犯。
提供分析报告,以确定哪些进程和用户占用系统资源。
提供本地数据库审计不可用的审计线索的细节。
当敏感数据发生变化时,提供能够生成对关键人员生成电子邮件警报。
解放了DBA,不再需要创建和管理用于数据更改审计目的精心调校的数据库触发器。
支持灵活的审计配置,使安全人员可以选择必须监督和审计跟踪记录的数据库操作和数据修改的特定类型。
对现有的应用程序提供完全透明的系统级和数据更改审计,无需任何修改这些应用。
完全兼容所有主机操作系统可以运行支持的数据库,包括但不限于Windows NT,UNIX和Linux,虚拟机,OS/390,z/OS。DB Audit 在多种平台,多种数据库上都有完整的解决方案:
安全性预防管理
侦测和安全配置分析
审计与监控
弱点及渗入测试
校正多种数据库统一管理,操作简便学习周期短,方便使用。通过左侧数据库树型目录可以方便管理各种数据库;右侧大块的工作区域中,将所有的审计按功能分类,可清晰地完成所有的配置。
DB Audit 可以出色的工作在多种平台,多数据库的复杂环境中,通过警告中心服务器收集、存储和分析各种数据库的审计警告,并按照管理中心所配置将审计报表或警告发送到不同的部门及用户。
DB Audit客户:
DB Audit拥有众多大客户,例如,M&T银行,道琼斯公司,富士银行(Fuji Bank),亨廷顿银行(Huntington Bank),Wells Fargo银行,北方信托公司, (The Reserve Funds)储备基金,第一资本金融公司(Capital One Financial Corp.),3M公司,AT&T公司,IBM公司,戴尔公司,JP摩根大通,惠普,壳牌,索尼,美国军队,美国航空航天局等。
软件截图:
DB Audit 目前在国内有一家授权代理 北京铸锐数码科技。
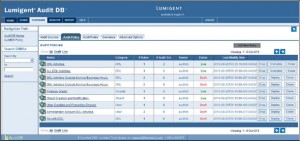
Audit DB – LuMigent 公司的产品 , 功能包括 数据库活动监控、审计、 用户权限监控、变更复核、访问监控等。
产品主页: http://www.lumigent.com/products/audit-db
软件截图:
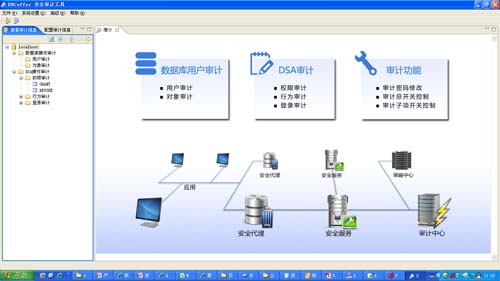
DBCoffer – 难得一见的国产数据库安全产品。 相关介绍: 国内首款主动预防型 数据库安全加固产品,存储层、数据访问层、应用访问层全方位防止数据泄密。
xSecure系列致力于对数据库的全面安全防护,覆盖数据库安全的事前检查、事中控制和事后追踪,形成面向用户的全方位的数据库安全产品和解决方案。
漏洞扫描产品xSecure-DBScan,实现对国际国内主流数据库的安全检查、漏洞分析和模拟渗透攻击,提供数据库安全状况检测评估报告和数据库安全加固建议。
核心功能:
数据库漏洞检查
覆盖绝大多数主流数据库的漏洞检查,包括:缺省配置检查、弱口令检查、无用对象检查、弱安全策略检查、SQL注入检查、缓冲区溢出检查、拒绝服务检查、宽泛权限、数据库补丁检查。
模拟渗透攻击
模拟黑客使用的漏洞发现技术和攻击手段,在没有授权的情况下,对目标数据库的安全性作深入的探测分析,并实施无害攻击(不会导致停机或对数据库造成损害),如获得系统权限、执行系统命令,篡改数据等。
检查报告
对检查结果进行汇总,提供不同类别、不同风险等级等因素的对比分析、趋势分析。
漏洞修复建议
能够智能化的协助网络安全管理人员评估数据库系统的安全状况,可以自动化地修复部分漏洞。
产品主页: http://www.schina.cn/a/fangan/shujukubaoxianxiang/about.html
www.askmac.cn Here